Kiosk Breakouts With the WiFi Pineapple
Sep 23, 2023
8 mins read
In this blog post, I’ll go over how I managed to partially escape a kiosk-like screen by using a WiFi Pineapple and a handful of its features. At the very end, I’ll get the browser equivalent of Doom running on the kiosk.
DISCLAIMER: I am not responsible for any warranty voiding or other damages caused by doing this. I can say this is ‘for educational purposes only’ and now I can say whatever I want, right? Right?
The Kiosk
This is a Hydrow:

It’s an indoor interactive rowing machine with a touch screen display. Via the display, you can watch recorded or live rows for your workout session and row along with an instructor.
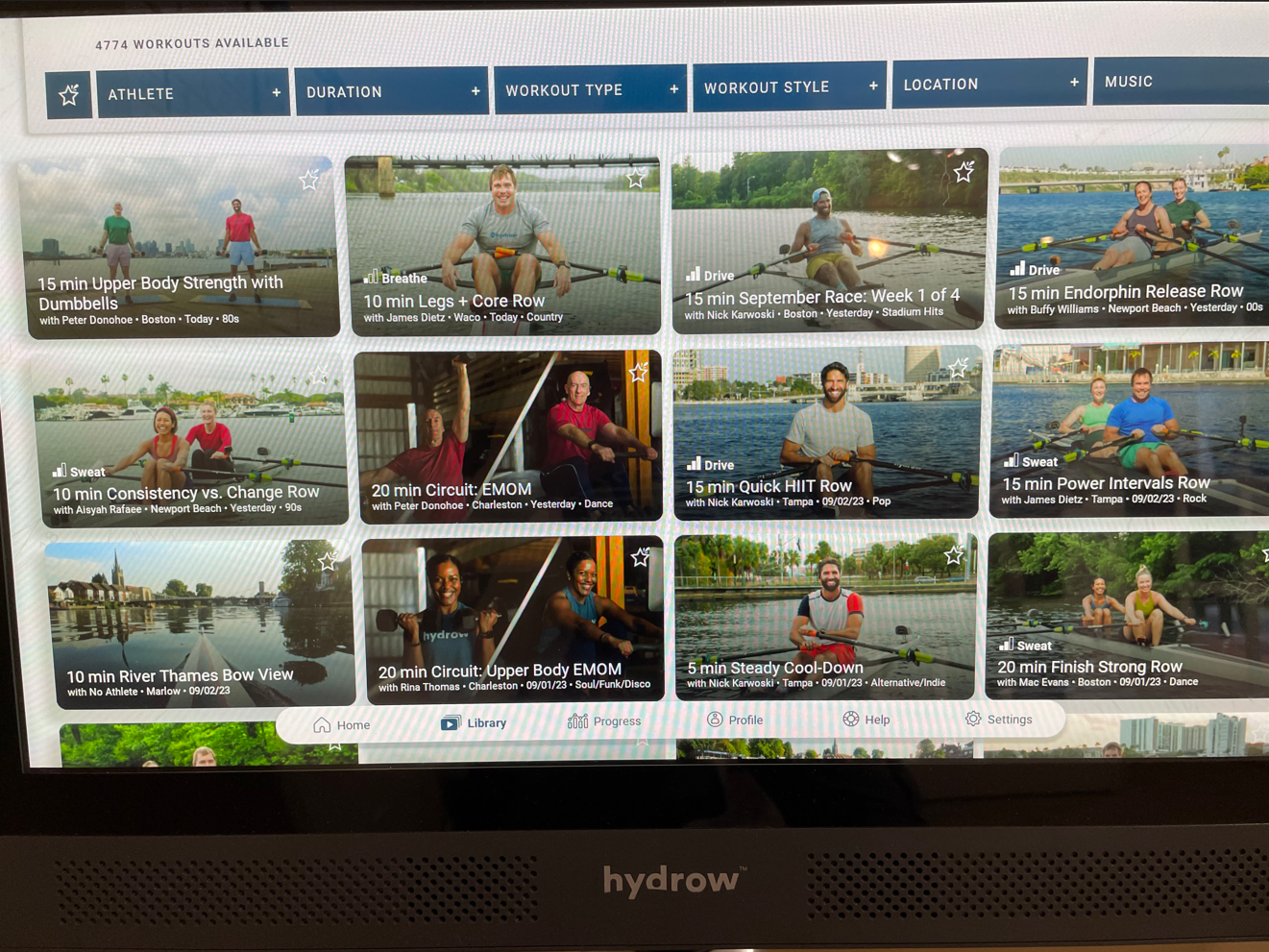
The Hydrow display is locked down and prevents you from accessing anything other than the Hydrow app. There isn’t a web browser available to watch YouTube or Netflix. Why? I don’t know. Anyways, I thought it would be fun to try and break out of the kiosk without having to rip off the back screen.
Second Disclaimer: No Hydrows were harmed in the making of this blog.
Messing Around
The first step of kiosk breakouts is “tap on everything you can find and hope something interesting happens.” I guess the Hydrow creators thought of this sophisticated idea themselves so there’s not a lot of interesting behavior you can get going. For instance, my first idea of finding clickable links in the terms of service didn’t work:
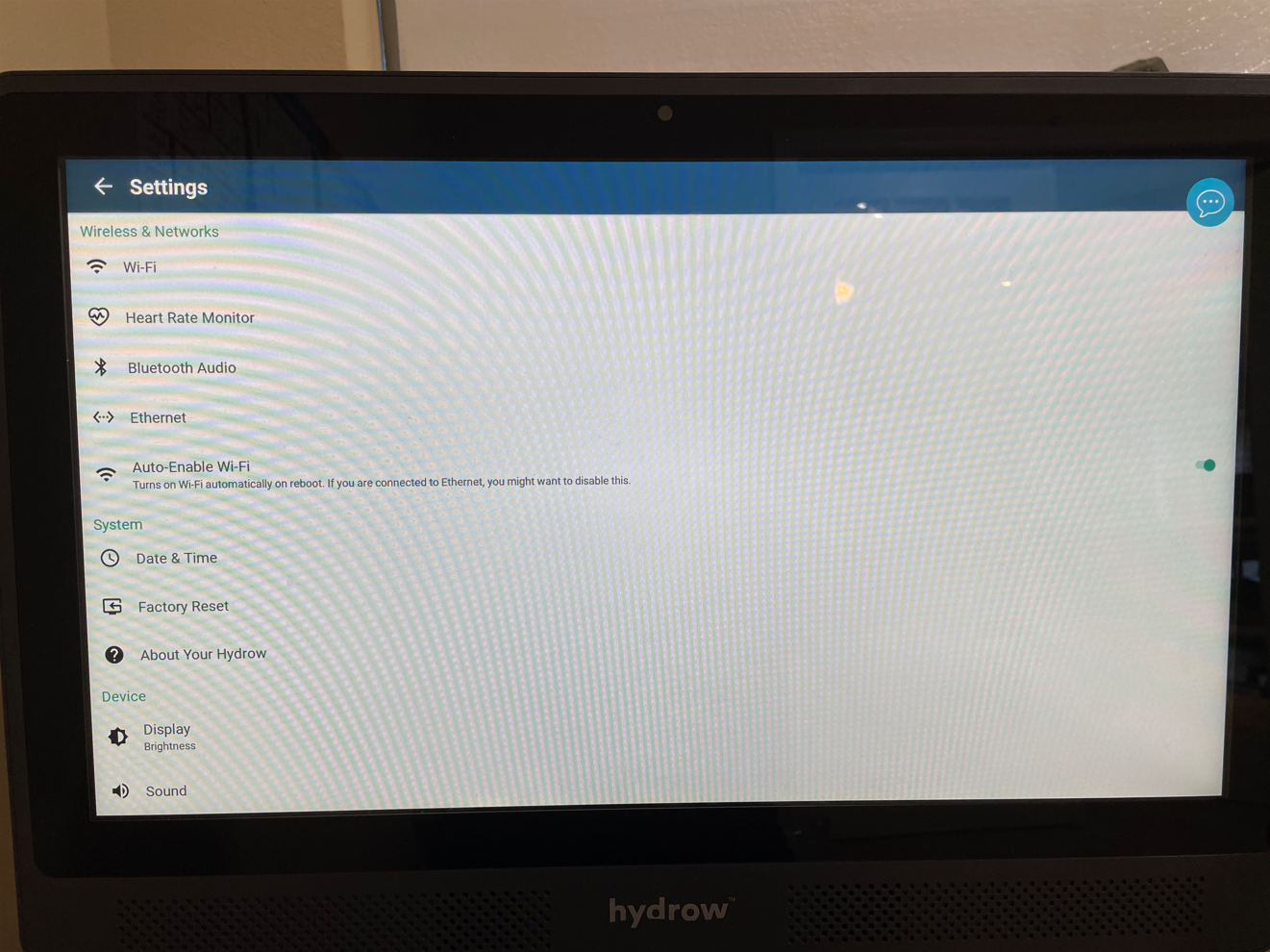
I did find some interesting behavior in the settings. I found a button in the WiFi settings to install a certificate, which clicking gave me a small peek into the filesystem of the Hydrow:
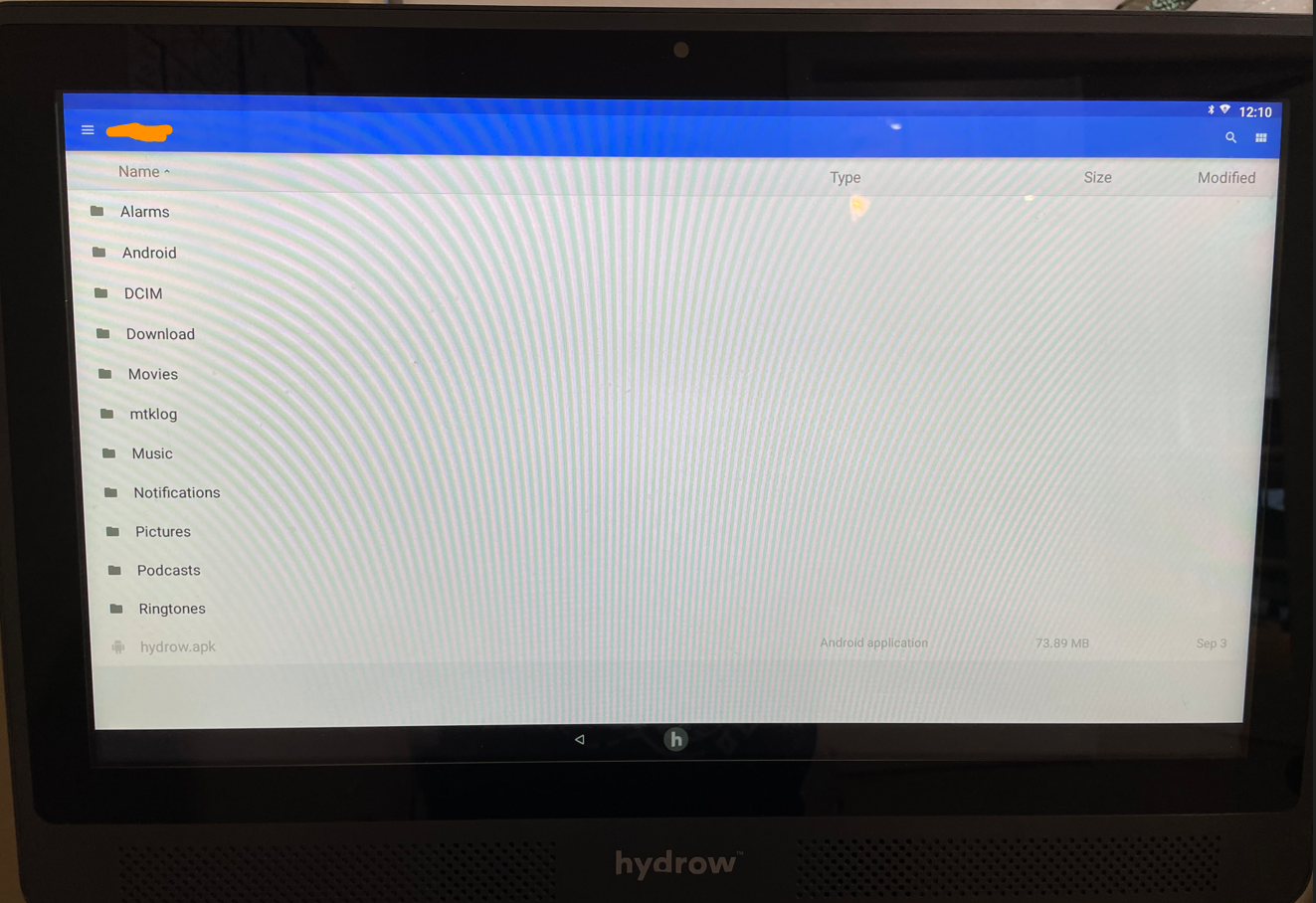 We can guess the app running the main kiosk service is the
We can guess the app running the main kiosk service is the hydrow.apk file at the bottom. I could browse around the folders, but I couldn’t open any of the files — meaning this was effectively useless. What next?
Educated Messing
With my goal to open YouTube or a similar website, I knew I had to start with opening a browser. But how? I thought back to the time when I connected to some airport’s public WiFi. Upon connecting, my browser immediately opened up to a page like this:
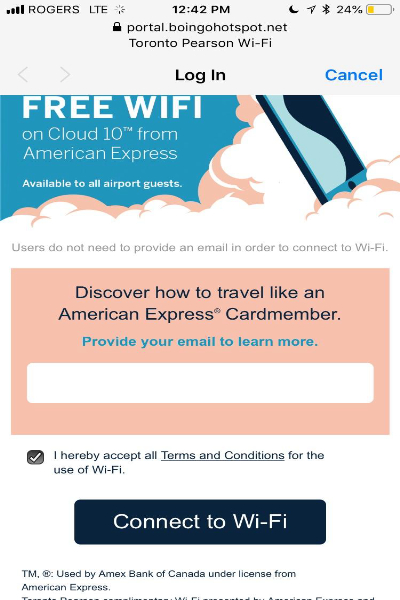
This is something known as a ‘captive portal’. Captive portals are webservers that open up after connecting to public wifi, usually with the intent of asking for further authentication before being given wifi access. I then wondered if the Hydrow would also open up one of these, giving me access to the browser!
Sadly, I don’t have any public wifi hotspots near my house. That means I have two options:
- Drive around with a Hydrow in my trunk for 2 hours in hope of connecting to a WiFi hotspot that has a google link in its captive portal
- Create my own hotspot with a captive portal for the Hydrow to connect to, and place a google link at the captive portal.
The former is incomprehensibly stupid, and I remembered I have just the tool to do the latter..

The WiFi Pineapple
The WiFi Pineapple is a very cool piece of equipment sold by Hak5. You’ve probably heard of it. If you haven’t, it’s a modified access point that simplifies all the malicious attacks you can do with having one. You can setup a wifi hotspot that MITMs traffic, captures traffic, and hosts malicious captive portals all from a web interface!
Captive Portal Setup
To add a captive portal to our Pineapple we’ll be using the ‘EvilPortal’ module. With the click of a button, the module will enable a captive portal webserver on our hotspot that we can edit to our desire. Here’s what the interface looks like:
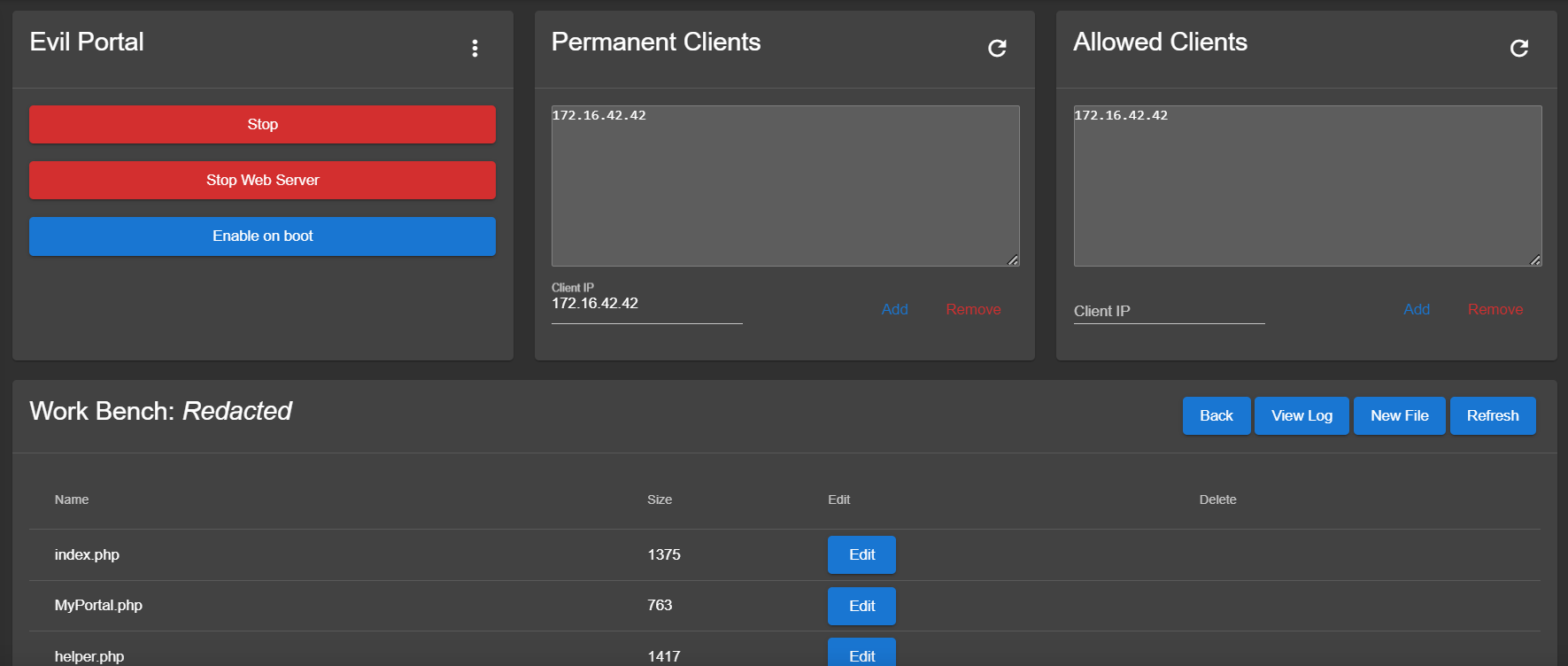 I enabled the portal and connected to the hotspot on the Hydrow. The portal immediately popped up:
I enabled the portal and connected to the hotspot on the Hydrow. The portal immediately popped up:
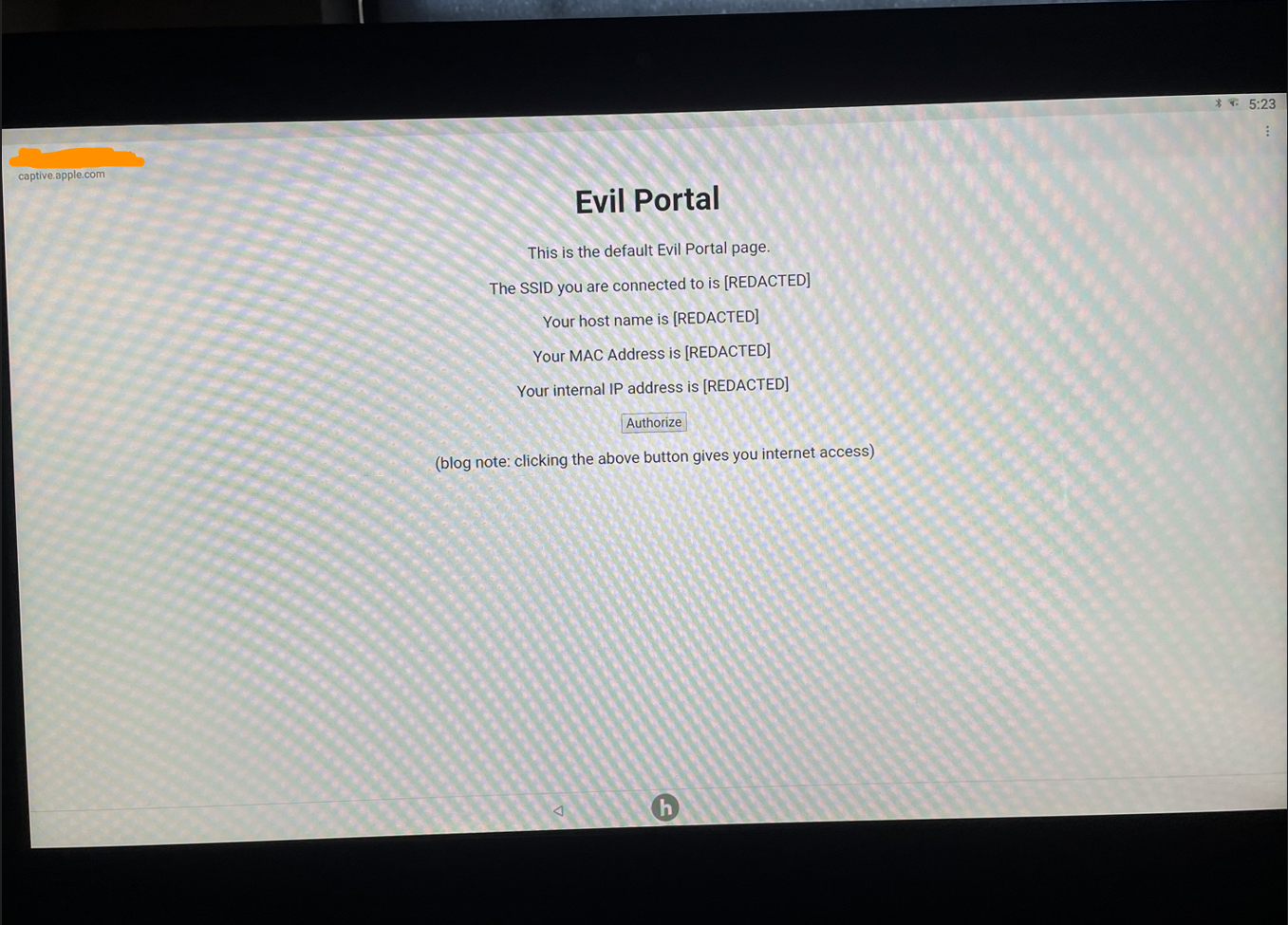
Awesome! Since we can edit the webpage as we desire, we should just be able to edit in a hyperlink to Google and get the jailbreak we wanted, right?
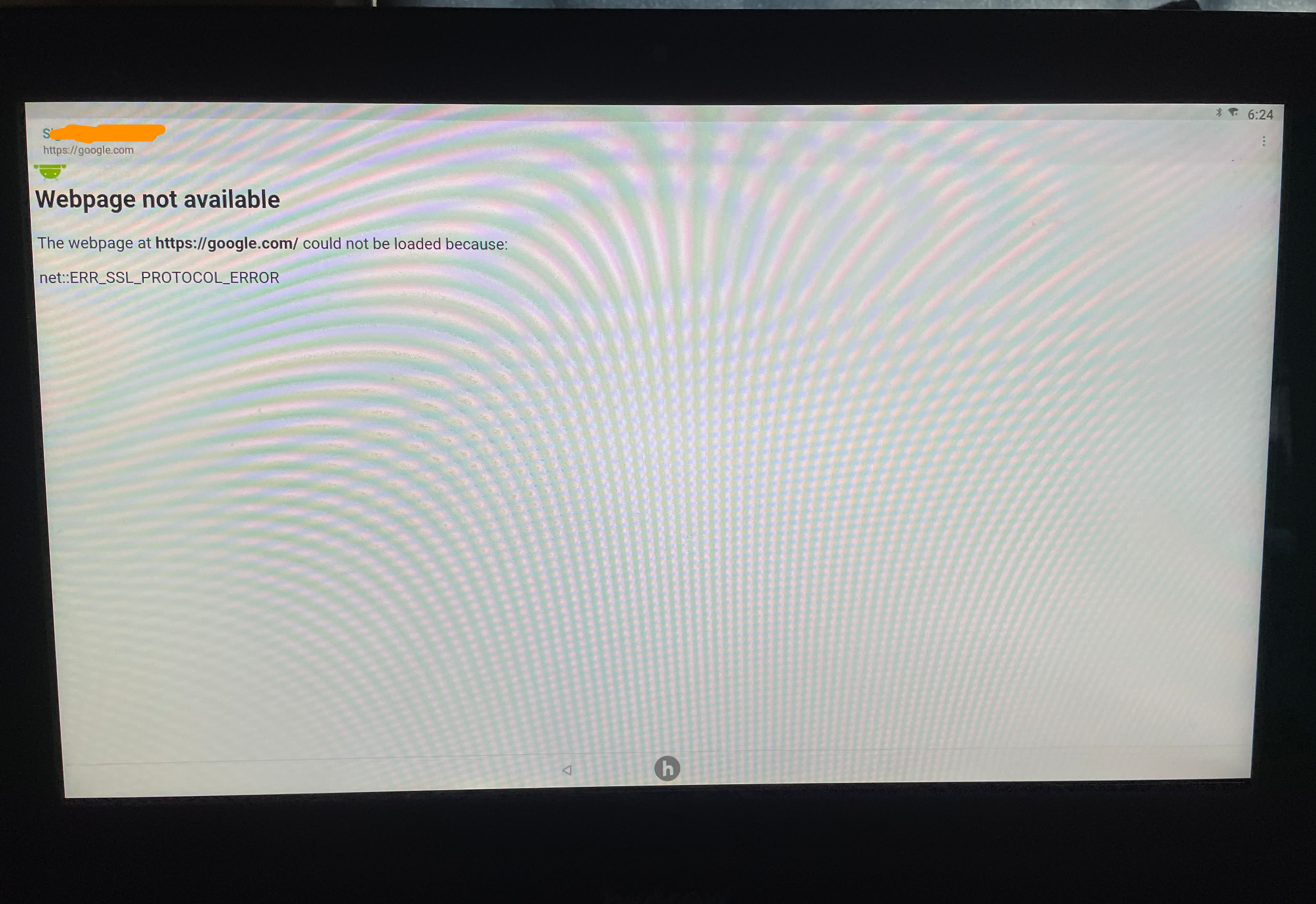
Nope. Since we haven’t clicked the ‘Authorize’ button on the portal’s homepage, our internet access is limited to the webserver only. Maybe we can click said button and click the Google hyperlink immediately after? I tried just that, and..
Nope. The second the Hydrow realizes we have a working internet connection we get kicked out of the browser and back to the settings screen. If we want access to the internet, we’re met with two options like before:
- Setup a proxy server on the captive portal to access the internet through it
- Trick Hydrow into thinking we don’t have internet when we actually do
Similar to the previous dilemma, the former option isn’t great. It could work, but it would be annoying to setup and put the Pineapple’s CPU under a ton of stress. The latter option also sounds much, much cooler.
Connection Check Reversing
How would we trick the Hydrow (which is really just an Android) into not having internet when it actually does? Well, let’s first try and figure out how it checks for an internet connection. To do that, I used the ’tcpdump’ module on the Pineapple which lets you capture packets of connected clients through a GUI. I turned on the module, connected to the hotspot on the Hydrow, and viewed the resulting packets in Wireshark. The connection check was then made obvious:
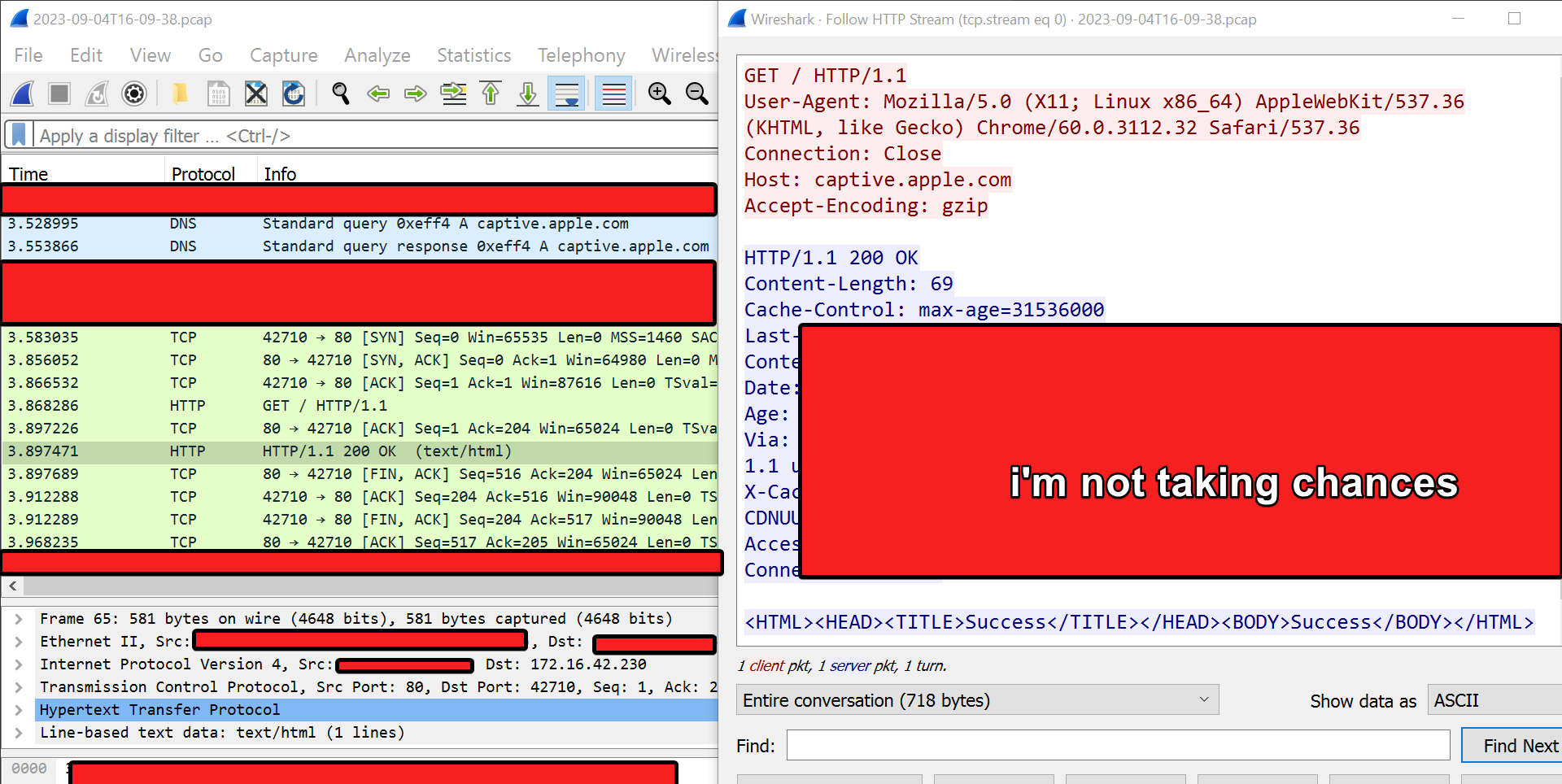 Upon connecting to the hotspot, it makes a request to
Upon connecting to the hotspot, it makes a request to http://captive.apple.com. If the site responds with Success (which is its regular response), then it knows it has internet access and immediately exits itself out of the browser. If it receives no response or a different one, then it assumes it doesn’t have internet access or is instead reaching the captive portal.
Connection Check Spoofing
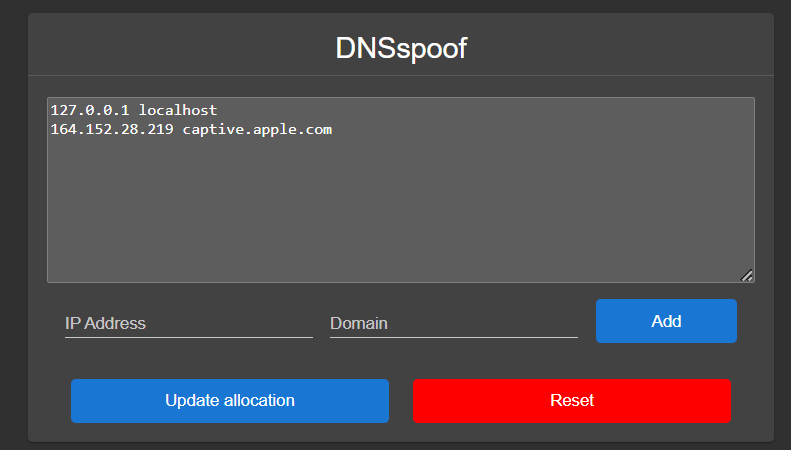
Since we control the access point, we can edit any packet sent/recieved to our desire. The DNS request for captive.apple.com is an easy target, because we can perform a DNS spoofing attack on it. If you don’t know how that works, DNS spoofing abuses the fact that DNS responses are unencrypted, meaning an attacker with the capability to edit others’ packets on the network can change the DNS response to whatever they want. Since we control the access point, we can very much do that! That means we can make captive.apple.com resolve to an IP that doesn’t have a webserver running. When the Hydrow sends a request to that IP, it won’t get a response back, and that might just trick the Hydrow into thinking it doesn’t have internet yet. The Pineapple module DNSspoof again simplifies this for us with a simple interface to perform spoofing. Here I’ve set captive.apple.com to resolve to a random IP that doesn’t have a web server running:
 With our attack setup, let’s give the jailbreak another try. I click on ‘Authorize’ like before, wait for the page to refresh, and I haven’t been kicked out of the browser! I click on the Google hyperlink I added, and…
With our attack setup, let’s give the jailbreak another try. I click on ‘Authorize’ like before, wait for the page to refresh, and I haven’t been kicked out of the browser! I click on the Google hyperlink I added, and…
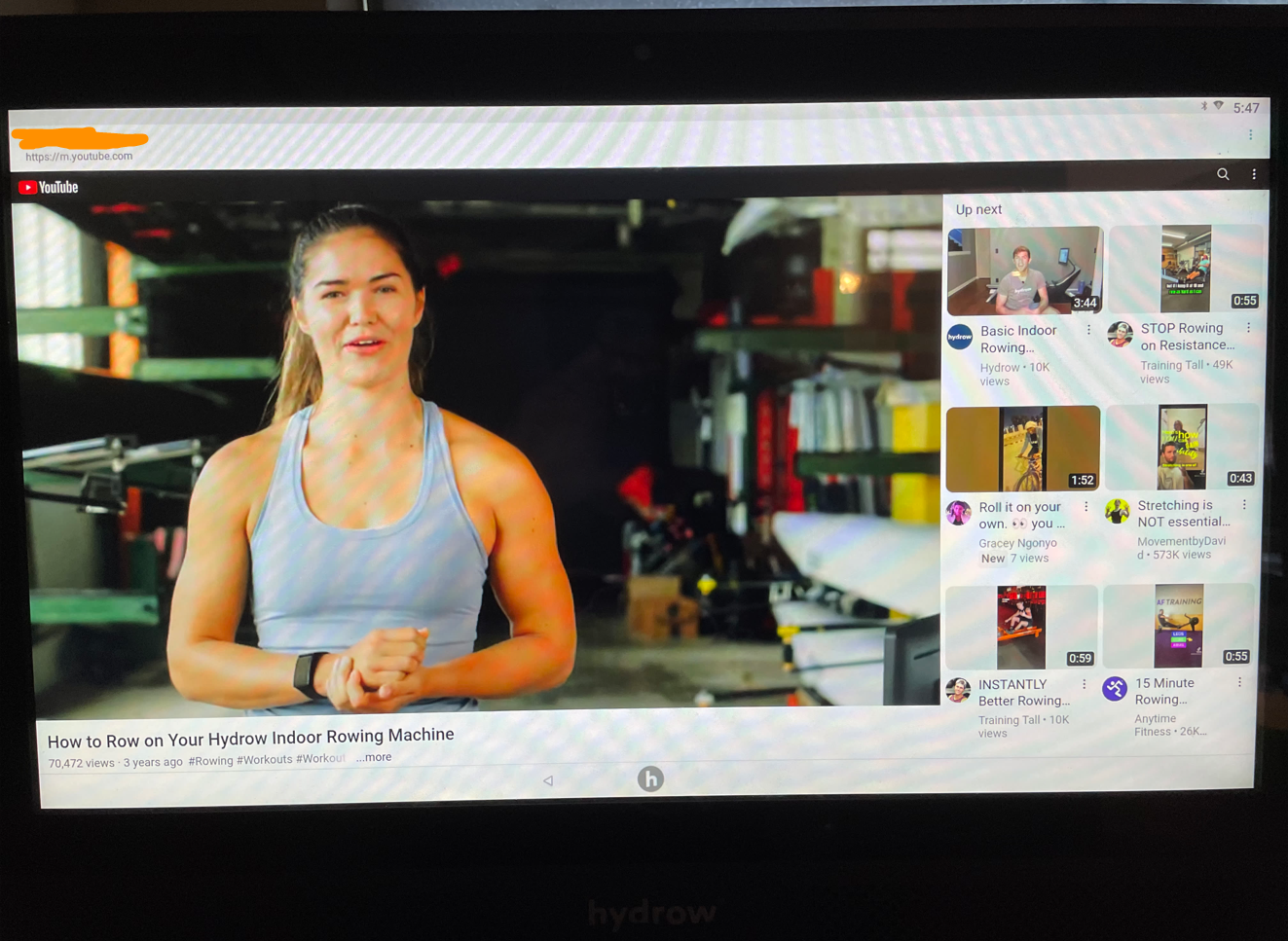
 Nice. Now I can finally learn how to use my Hydrow!
Nice. Now I can finally learn how to use my Hydrow!
‘Okay So Why Did You Actually Do This’, and a new litmus test
I have a reason I went through all this trouble to get a browser working on the Hydrow. A very good reason, in fact.
I think most people nowadays have heard of the whole ‘can it run Doom’ meme? If you haven’t, hardware hackers have been modifying systems that really shouldn’t be running the game Doom to, well, run Doom. You might’ve heard of when Foone got it working on a pregnancy test or of the DEFCON30 presentation on jailbreaking John Deere tractors which ended with some Doom gameplay.
I propose an easier one for kiosk breakouts: “Has someone beaten Sans on it?” There’s a website containing an accurate simulation of the boss fight from Undertale, meaning anything that has a web browser (so, most kiosks) can participate in this without having to rip off its back panel. I credit my brother for this, who I saw attempting to get the fight to load on our Wii. I was inspired and we started hunting down other devices that could have a browser in them. Once I discovered the Hydrow jailbreak, I handed it over to my brother, and an hour or two later…
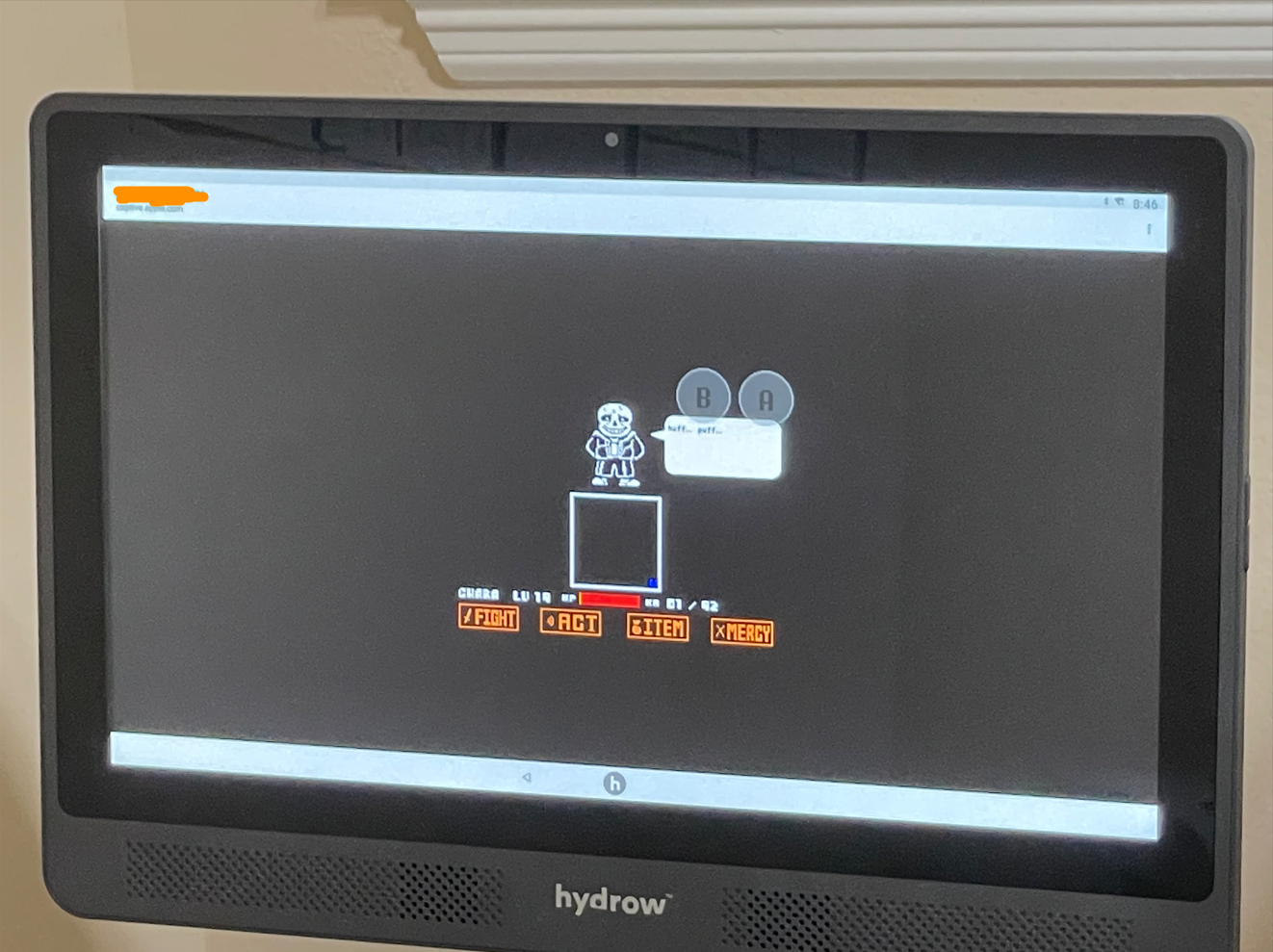 So yeah. If you can finish this fight on anything stupid, including non-kiosk (like an interactive refrigerator door), an email/DM to me would be greatly appreciated. My contact info is on the home page.
So yeah. If you can finish this fight on anything stupid, including non-kiosk (like an interactive refrigerator door), an email/DM to me would be greatly appreciated. My contact info is on the home page.
Sharing is caring!